Site PGP Signature
Public Key
https://nationalradical.com
http://jymfasyfmxn2ytc5poswetilpplct6h54y7ih3enyn46tqvssegxvlqd.onion
TOR - The Onion Router
Standard Internet Traffic
To understand Tor it's useful to understand how interacting with web browsers and the modern internet works, from there it's easier to explain how & why Tor does what it does and why Nationalists should adopt this tool for radical activity. While it's impossible to go over every aspect of the internet, I'm going to focus on the key components and ignore overly technical details such as routing, DNS, IPV6, protocols, and ISP tiers.
To interact with the internet you send data and receive data. For example if you want to view a website, you're requesting content from that site's servers and it is in turn sending the requested content back (should everything be working). This is done using IP addresses. In short every home, school, or business has a unique outward facing IP address, so does every server that is hosting content & websites. These IP addresses typically look like 90.123.33.222, four numbers between 1-255, split up by dots. To interact with a website you send information to a server (a request), and it gets routed through ISPs, Servers, and other service providers.
In the below image, the end system is your home computer, ISP is your internet service provider (eg. Verizon), and the End System (Server) is the website you're connecting to. As a note the data being sent/received is encrypted with TLS when using HTTPS websites, and not encrypted with HTTP websites.
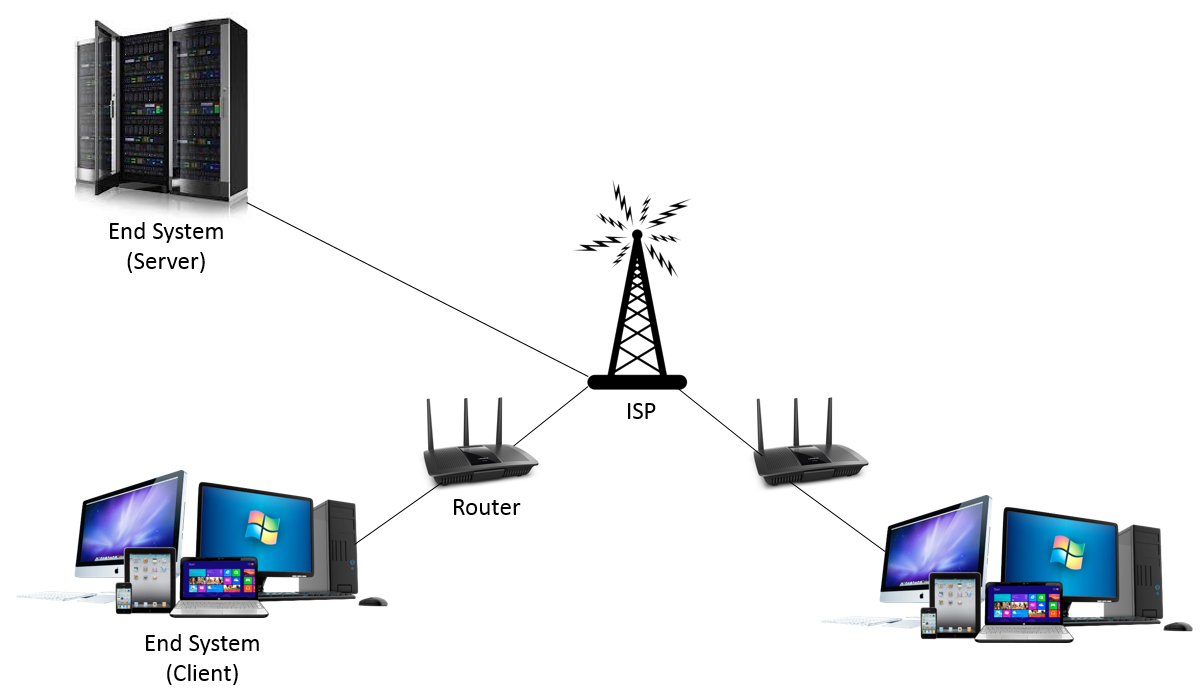
This system works for most basic needs, but when it comes to security and privacy it's not great.
For starters every server you interact with knows your unique IP address, this can be linked quite directly to you. Your internet provider as well as the web server almost always store this information and will hand it over to law enforcement upon request.
Secondly, there is an enormous amount of tracking that goes on with the modern web. This tracking is done for several reasons such as optimizing advertisements, stopping spam, and personalizing the websites experience to you. This tracking aggregates so much information from cookies and other tools that basically every where you go online you're being tracked. Information tracked may include search history, IP addresses, Operating System, Browser Version, Screen Size, and a number of other factors. Using these attributes websites and advertisers (and governments) can somewhat effectively build a 'fingerprint' by looking across these attributes.
VPNs
It's good to want to improve your security, and in response to the clear problems with standard web browsing people look to solutions like VPNs. Chances are you've seen an ad for one on youtube, but how do they work? VPNs are very simple, using one will cause your computer to route network traffic to a VPN Server which will then route it to the website or service you want to use. Below is how VPN routing works compared with standard internet usage.
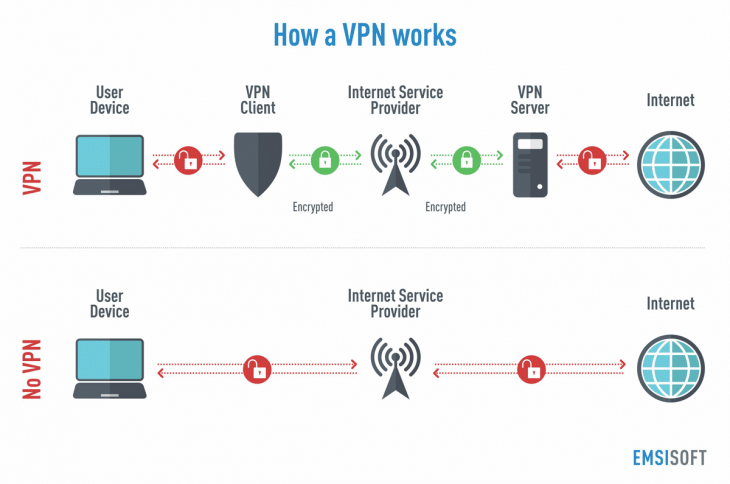
At first glance, you may think this has solved the privacy/security issues that exist, and while certainly a slight improvement there are still a large number of issues.
One of the biggest issues is that you're placing your faith entirely in the VPN company you choose as you're connecting to their service on your home IP address (which can be linked directly to you) and they at least can save information on every IP address/website you connect to. You really can't know what they track, they can claim to not keep logs but there's really no way of verifying this. VPN providers have handed over these types of logs to law enforcement before (despite saying they didn't keep logs) and it has directly led to people being arrested [1].
Another key issue is that an incredible degree of care must be put into not making mistakes with VPNs. For example logging into your personal email address using a VPN that you also used for radical/dissident political activity may lead to you getting identified as those can be cross referenced. In the previous link [1] after getting logs from the VPN provider they saw he had logged into his real gmail and other services on the same IP he had used for criminal behavior.
The final big issue is that this does nothing to address browser tracking, your browser is still logging and tracking a huge amount of information via cookies and other sources. If you're connecting and disconnecting to a VPN, while using the same browser that's pretty easy to see for those tracking that you're the same person. This is a pretty obvious problem
What is Tor
With these issues in mind, what's Tor's solution and why should it be trusted?
Networking
Tor's solution to secure networking is where it gets it's name (The Onion Router). The core idea of the Tor Network is to make connections through layers (similar to an onion) of network encryption where each layer passes to the next. When doing this each layer, which is called a node, only knows where it got the data and where to pass the to next. This data is protected via encryption, where a node can only decrypt it's part of the chain, creating a secure layered encryption. Once it makes it through the chain of nodes, that final node has decrypted the last layer and knows which website to interact with. The final node can then send the request to the website and in turn passes any response back through the chain with a similar layered encryption. The website only interacts with the final node (so doesn't know who you are) and the exit node has no idea who you are either as its just connecting to the node before it.
The below example shows this encrypted layering well. In this image you are the source, making a request to a website via the Tor network, that request is the message. The message gets 3 layers of encryption A, B, and C. The data gets passed to Node A which doesn't know what the request is but can decrypt its part and see it needs to send it to Node B. Node B gets the message and can't decrypt the message, but can decrypt its part and see it needs to send it to Node C. Node C gets the data decrypts it and can then send it to the website, sending any response back down the chain with a similar layered encryption.
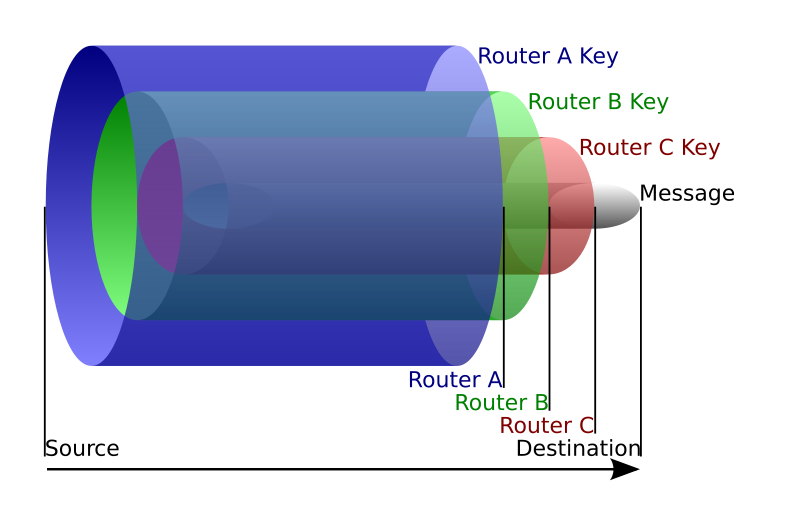
Nodes are run by volunteers who support the network. There are thousands (8,000 at the time of writing this) of nodes, meaning each time you load up tor or request a new Tor network circuit, you're going to get a new circuit path. This is where Tor gets its resilience to state surveillance, for someone to see which website you're interacting with they would have to control all nodes in the chain. With the number of nodes there are, this is near impossible. While an extremely powerful adversary could spin up thousands of nodes, the number of active nodes is closely tracked by users and would be a glaringly obvious attack which would be responded to.
There are three main types of Tor Nodes. There is one other kind of node, called a bridge. I'll touch on this later as it's a bit different from the other nodes in a circuit. They are
- Guard Nodes - These are nodes you connect to, they form the start of the Tor onion routing
- Relay 'Middle' Nodes - These are nodes that form the chain between Guard and the final Exit Node, you never directly connect to these and due to the guard, they never know your IP Address.
- Exit Nodes - These are the final node in the chain and what is making the actual connection to a website, meaning the exit node IP is the IP address the website sees. Exit nodes never know your IP address.
Below is an example of loading a website using a Tor circuit. With the User on the left connecting to a Guard, which connects to a Middle relay, which then makes a connection to the exit node, which makes the final request to the website's server.
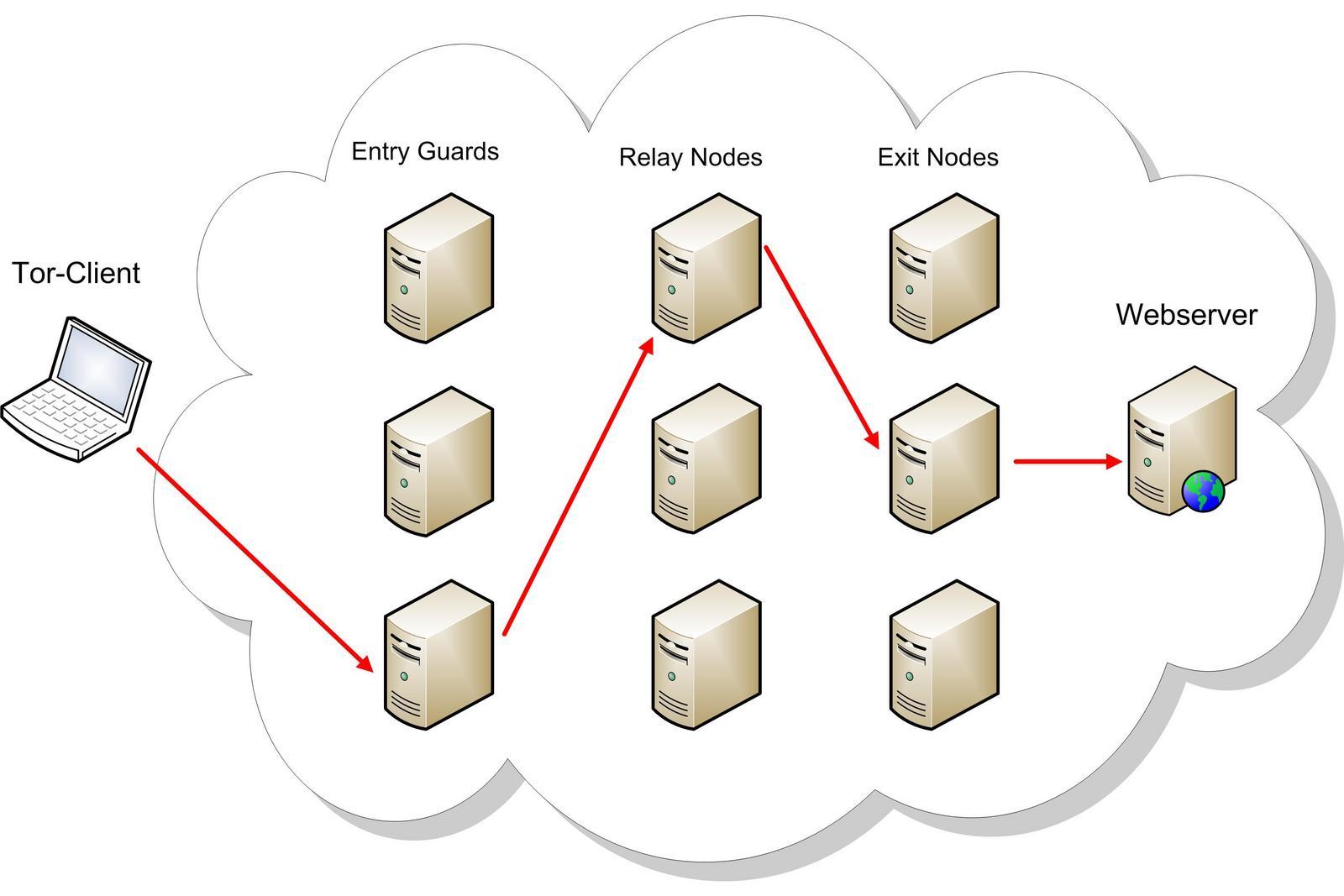
Hidden Services
The Tor network also has a different kind of website that is only accessible via the Tor network called hidden services. These websites collectively are typically called 'the dark net' as they are not accessible via standard browsers, conversely the normal internet is sometimes called the clearnet. There are a variety of websites running on the dark net such as dark net markets (where credit cards, drugs, and other illegal items are sold), political websites (like National Radical), and mirrors of normal clearnet websites. Unlike a standard website that has an open IP address the world can see, hidden service's IP addresses are hidden and protected behind the same Tor network routing mentioned above. This creates a significantly more private un-censorable internet for content that may be more radical or illegal. Additionally the encryption used on hidden services is public key encryption that is more secure than TLS encryption used on HTTPS websites and does not have an outside party involved such as a certificate authority.
When available you should use the hidden services as they are more secure/private. When a clearnet site offers a hidden service it will appear as a purple ".onion available" on the right side of the URL bar in Tor Browser, clicking on that will load the hidden service for that website. A directory of some hidden services can be found at dark.fail (hidden service http://darkfailenbsdla5mal2mxn2uz66od5vtzd5qozslagrfzachha3f3id.onion/)
Browser
The main way of interacting with the Tor Network is the Tor Browser. This browser is available on all platforms (Mac/Windows/Linux/Android/IOS) and handles all of the network details of generating tor circuits and making connections. In addition to the networking Tor Browser is designed to solve the issues previously mentioned about browsers and tracking. Tor Browser is designed for anti-fingerprinting, meaning that it limits information given to websites, with the information that it does provide being the same for all Tor browser users. This means while you cannot hide that you are connecting a website you're connecting to it, you blend in with all others who Tor.
Tor Browser also comes with a number of features like easily changeable security levels and identity reset. The security level modifications can be used if browsing an unfamiliar or sketchy site, you can quickly upgrade your security to limit what can be served to you in the browser, for example limiting 'Safer' mode limits audio/video autoplay and Javascript on HTTPS sites. The identity reset functionality can be used if you have concerns about cookies or other trackers on websites, when used it restarts the browser with a new Tor connection circuit and the cookies/cache cleared. This feature can also be used when switching tasks, for example if you were researching a radical topic for some time but then wanted to use a popular service or look at mainstream information, by resetting your identity you cut off the ability for advertisers or governments to track and aggregate all that together.
Using Tor browser also allows for great compartmentalization of activity and data. By using a standard browser (Chrome/Brave/Firefox) for your bank account, school, or paying bills while confining radical activity to Tor Browser you keep the network and connectivity records for those tasks separate, meaning they can't be combined to identify you. For example in the previously mentioned example (the individual who was on a VPN and connected to his Gmail and also alleged criminal activity), if he had confined his sensitive alleged criminal activity to the Tor Browser and Gmail to a standard browser then those IP logs could have never been cross referenced.
Limitations
It's important to know the limitations of Tor for proper use.
- Network owners can see you are connecting to Tor
- Due to the nature of all nodes being public so you can generate Tor circuits, it's possible to see all of their IP addresses and associate them with Tor network usage
- This means network managers (people with admin rights on the router or system of routers) such as an IT department at a University or Office can see that connections to Tor are being made from your computer
- This does not mean they can see what websites you're viewing or what you're sending to those websites. This information is encrypted and can't be read. They just know you're connected to the network, as well potentially knowing the amount of time and bandwidth you use with that connection
- There is an example in the case studies below of where this came into play (Harvard bomb threat guy). Note with this case, the individuals Tor usage (websites/logins/requests) wasn't compromised, just that he had been using it at a specific time. Had he shut his mouth and not talked to the pigs, he would have avoided prison.
- There is a solution to this called bridges which is discussed in the next section. These are the final kind of nodes that can hide connections to Tor and avoid people blocking the Tor network. There is some trade offs with these as is discussed.
- Tor is slow(er)
- As a result of routing all connectivity through several servers across the globe Tor is slower than a the connection speed in a standard web browser.
- While a limitation, this is completely worth it for the level of security Tor provides
- Browsing may be somewhat limited
- As exit nodes IP addresses are all public, some websites will block them due to spam and other reasons. This may mean you'll be blocked from viewing some sites. Other sites may take a softer approach and require a captcha for you to view the site.
- Solving captchas is worth the security that Tor provides
- If you need to view a specific site that's blocking you, try creating new Tor circuit (done in the options) to see if they've just blocked the exit node you're on currently. Alternatively, you can use an archiving service like wayback.archive.org or archive.is to view (or create an archive to view) the site you wish to see.
- Tor shouldn't be used to Torrent
- Torrenting (which you may be familiar from sites like piratebay) is a useful tool for decentralized file sharing and resistance to censorship.
- Using Tor to Torrent is bad for the network and may allow you to be tracked due to how torrent tracking works (read https://blog.torproject.org/bittorrent-over-tor-isnt-good-idea/ for more info)
- Tor won't fix basic stupidity with what you share.
- Tor is very sophisticated and secure, but if you use it like an idiot it won't help.
- Keep information about who you are to yourself and don't re-use usernames/passwords and other information.
- Be very conscious about what you're saving related to Tor usage that could be used against you, for example saving Tor hidden service links on a notepad or text file is very insecure (Tails is a great solution for this)
- Don't brag or tell others about your activity using Tor.
- Several case studies of people who were arrested for criminal activity that used Tor are mentioned at the bottom of this post (Spoiler: most made basic dumb opsec mistakes with information they shared that caused their arrest/downfall)
Bridges
As previously mentioned IP addresses of standard Tor nodes are all public. This is so when connecting, Tor can create a random circuit for your use. As a direct consequence of this, should a government or network provider (university, business, ISP, etc) wish to block the use of the Tor network, they can download that list of IP addresses and block the connection to all of them. They could alternatively not block them and monitor network traffic for anyone making connections to these IP addresses. This is where bridges come in to play.
Bridges are essentially Tor nodes that are not public (and as such cannot be blocked/tracked). When setup, before connecting to a standard Tor Guard node, you connect to a bridge and get around any blocking or monitoring that may be happening. There are a decent number of them, currently around 2,000 are online.
You should consider using Bridges anytime your network may be monitored or Tor is being blocked for you. The downside of bridges is pretty simple, it's just going to slow your connection speed down a bit as you're making another connection to get to Tor.
To obtain a Tor Bridge you can go to https://bridges.torproject.org/options/ and click Give me bridges, do the captcha, and save your bridge information.
How & When to use Tor
The basic usage is pretty simple, download the Tor Browser on whatever platform your on and install it. The website to download can be found here https://www.torproject.org/download/. Once you download and install it, you'll notice it's pretty similar to a standard web browser (as it's based on Firefox) and is pretty simple to use.
Alternatively if you have higher security needs you should consider downloading and installing the Tails operating system. I've written a sister article to this one explaining what Tails is and how it's the most secure operating system to use for radical political behavior. With Tails, Tor is integrated within the OS, so all network connectivity goes through Tor. Tails has a huge number of other security features like persistent storage to store encrypted files and notes that make it the best secure option. You can read that here
You should use Tor when talking about or engaged in anything radical or dissident but not when doing everyday normal internet things. This process as previously mentioned is called compartmentalization. If you're logging into your bank account, or your school blackboard, or your Facebook (please stop using Facebook) then use a everyday normal web browser like chrome. If you're logging in to read radical content, to post or interact with other radicals, or sharing radical content with the public then confine that entirely to the Tor Browser, or depending security risks confine it to Tails.
Please keep in mind when using Tor, that it will keep your connectivity and networking safe, but if mistakes are made outside of that then they may cause you issues. Please read the next section which lists a number of case studies on people getting caught despite using Tor. One common theme you'll note is that it wasn't Tor that was the problem, it was actions/decisions done by the user.
Case studies
This section contains case studies of those who were caught despite using Tor. This is not an endorsement of their actions, more focused on examining their mistakes.
The Harvard bomb threat [2]
In 2013 a Harvard student emailed in a bomb threat to the school. He did this using Tor and an anonymous email service called guerrillamail. After getting the threat Harvard and the FBI got an IP address from the email headers. That IP address was of a Tor exit node. With this information they didn't have much to go on, however Harvard looked through their network logs. All students at Harvard are required to login to the network with their ID/personal credentials. Using the timestamps of the threat and the network logs they found that this student was the only one using Tor at the time of the threat. The FBI brought him in and despite the circumstantial evidence he confessed, he was federally charged for the crime.
Lessons
- Use a bridge. Using a bridge would have meant they wouldn't have been able to see that he was connected to Tor at the time of threat.
- Additionally using different Wifi network that wasn't owned by the specific people he was threatening (for example at a local coffee shop) may have avoided him being identified as a person of interest in the first place.
- Don't talk to the fucking pigs
- When he was brought in, they had barely even circumstantial evidence against him- just that he was using a network used by millions worldwide at the same time they got a threat.
- They absolutely would not have had enough to convict him if he didn't confess. They did not have proof he ever visited guerrillamail or sent the threat because of Tor's security.
- If you find yourself in a room with the cops or FBI pigs ask for a lawyer and then shut the fuck up.
DPR of the Silk Road [3]
'Dread Pirate Roberts' was a pseudonym used by the person running 'Silk Road' which was first dark net market (where drugs and other illegal items are bought/sold on the dark net) that got big. The site and the arrest have been covered extensively so I'm just going to touch on it briefly.
After the site got big, multiple government agencies were after the owner, but could not identify him. They found his server through coding mistakes in a captcha feature on the site, but still couldn't identify him.
An IRS agent found a very early post about the site on magic mushroom forum, the post was by a user called 'altoid'. The agent then found posts from an 'atloid' on a different forum looking for a web developer for the darknet where he listed his personal email address at the bottom of the post. This information was what led to him being caught, where he was arrested in a library while using Tor on his laptop.
He was arrested, charged, and was sentenced to life in prison for being a 'drug kingpin'
Lesson
- Be extremely careful how you talk/post about Tor & Darknet usage.
- Don't reuse usernames.
- People very often re-use usernames despite how easy it is to cross reference and link them. Never do this on Tor, especially not with usernames you've used in normal clearnet web browsing
- Consider your physical security when using Tor (& Tails)
- When he was arrested, police pulled him away from his laptop while it was logged in to make sure they got all the data from it.
- It's unknown how strong of case they would have had without what they accessed from his computer.
- Don't leave your computer unattended when doing anything radical with Tor. Close Tor when stepping away.
- Don't put yourself in a position where someone can be looking over your shoulder at what you're doing on Tor.
Alphabay [4]
The owner of a different dark net market known as Alphabay was caught more recently. He like DPR used Tor/Tails and kept good security for the most part. Alphabay became a massive website with 200,000 plus users and the feds had no clue who he was. Until they got a tip with an early email that Alphabay had sent to users. In the email headers the market admin used an email address that was directly tied to his real identity, While he later changed this mistake, this tip was enough for police to arrest him in Thailand. He killed himself in a Thai prison shortly after.
Lesson
- Compartmentalize your data
- Keep your personal email addresses off Tor. Create new email addresses (tutanota, skiff, proton) for Tor activities.
- It may be frustrating or slower to have to create new emails and new logins that are Tor specific, but they're absolutely worth the time. Do not get lazy, it will cost you. It may be more difficult to do things on Tor, like setting up an easy to use email, but take your time and get it done right, or don't do it all.
High school threats [5]
A student at a high school in Florida paid for a dark net market service that called in bomb threats to his school several times. While the threats were untraceable to him, as he was not directly doing them and his tor usage hid his connection to this market he was still caught. He was caught because he started telling friends about it, rumors began spreading, and when the police arrived his name was one of the first that came up among students. He then confessed to police what he had done.
Lessons
- Don't talk about illegal activity you're doing.
- This should be simple, but many people still make this mistake. Avoid this temptation as it will cost you.
- Don't talk to the police.
- Who knows what they would have had if he hadn't confessed. Avoid this stupidity. Don't talk to the pigs
Cyber Stalker [6]
There was an cyber stalker that would break into Facebook accounts and blackmail minor girls for more pornographic imagery. He was a target of the FBI for some time, but he used Tor (via Tails) to secure himself. The FBI with the assistance of Facebook developers planted a file for him to download, he downloaded it and opened it. That file had malware embedded into it that exploited a bug in software to 'phone home' and identify his IP address to the FBI.
He was then arrested and got 75 years.
Lessons
- Be very careful with what file(s) you download
- If you do need to view the files that have some risk, disconnect your device from the internet. If you're using the Tails OS, restart your machine after opening the file to reset the OS.
- For even more security, using a USB drive, move high risk files to a seperate device that is not connected to the internet (ideally running the Tails OS) and open the files there, this is called creating an air-gap.
- Make note that some file types are higher risk than others. Simple file types like text files have less security concerns than file types like videos, spreadsheets, and PDFs.
- In extreme cases do not use Tor from your home.
- He took many necesarry software security steps with Tor and Tails, but no software system is without bug or exploits.
- In extreme situations (i.e. if you're taking credit for an incredibly high profile action) it is useful to not make your connection at your home. Go to a Coffee shop, Library, or McDonalds parking lot. Connect to Tor, do what you have to and leave.
Freedom Hosting [7]
Freedom hosting was a darkweb hosting service that catered to child-porn websites. In 2013 the owner of the site was targeted by the FBI using a Javascript exploit that sent the user's Mac, IP, and Windows computer name.
The owner was eventually arrested in Ireland, extradicted and sentenced to 27 years.
Lessons
- Use Tails in high-risk environments
- While this exploit was patched, understand that no software is without bugs, limiting what happens if one component fails is important.
- This bug likely wouldn't have worked on Tails due to its OS level Tor integration and Mac address Spoofing
- Update Tails/Tor any time there is a new update
- At the time this exploit was done, the current version of Tor had patched the bug, meaning only users using an older version were vulnerable.
- Anytime there is an update in Tor or Tails, do the update. Often these updates are put out as soon as a bug or exploit is found.
Final Note
Tor is a time tested secure and anonymous network/browser used for interacting with the web. It is critical for any radical or revolutionary to integrate this into any web usage that supports their revolutionary activity should they wish to remain secure.
Keep in mind Tor is just a tool, that when used correctly[8] it works securely. When you make mistakes and make dumb decisions about what you share and do, the tool is worthless for its purpose. Please read the Tails Article for info on an operating system based around Tor that provides even more security.
References
[1] VPN Providers Shared Logs With the FBI - https://arstechnica.com/information-technology/2013/12/use-of-tor-helped-fbi-finger-bomb-hoax-suspect/
[2] Harvard Bomb Guy https://www.theverge.com/2013/12/18/5224130/fbi-agents-tracked-harvard-bomb-threats-across-tor
[3] Silk Road - https://www.youtube.com/watch?v=HBTYVVUBAGs
[4] AlphaBay - https://www.theregister.com/2017/07/20/alphabay_hotmail_fbi/
[5] High school threat guy - https://www.youtube.com/watch?v=GR_U0G-QGA0 (first section)
[6] Tails/Tor Cyber stalker - https://en.wikipedia.org/wiki/Buster_Hernandez
[7] Freedom Hosting - https://en.wikipedia.org/wiki/Freedom_Hosting#Federal_investigation
[8] Staying anonymous with Tor - https://support.torproject.org/faq/staying-anonymous/